Computer Forensics – Training Courses
What is Computer Forensics?
Computer Forensics, also known as Cyber Forensics refers to the analysis of information in the computer systems, with the objective of finding any digital evidence that can be used for legal proceedings, but also to discover the cause of an incident. Computer forensics is the process of extracting data and information from computer systems to function as digital evidence for civic purposes, or in most cases to prove and legally impeach cybercrime.
The purpose of computer forensics is to provide forensic practices, legal processes, and ethical principles to assure reliable and detailed digital evidence that can be used for the courtroom needs. The objective of computer forensics is to guarantee a well-structured investigation and a follow-up of processes in order to resolve incidents and malfunctions in an organization.
Why is Computer Forensics important for you?
A forensics process is applied after the cyber attack or incident has occurred in order to collect and analyze the data to determine what happened, how did it happen and why did it happen? Computer forensics can be used as a tool to exploit backdoors that should be patched. A computer forensics investigation is a proficient mechanism that allows organizations’ to rationalize their time and immense financial impacts.
An internationally recognized computer forensic professional will be able to provide a detailed investigation of computer systems and assist the law enforcement authorities. Computer forensics’ provide you with the advantage of learning and practicing the latest comprehensive security methodologies of network systems, encryption technology, file operating systems, and criminal science.
Benefits of Computer Forensics
- By becoming Certified Computer Forensics Professional you will be able to:
- Understand the role of computer forensics in the business world.
- Support an organization to prevent incident occurrence
- Learn the prime forensic skills that can be applied in different situations.
- Improve your forensic techniques and tools to identify and respond to cyber
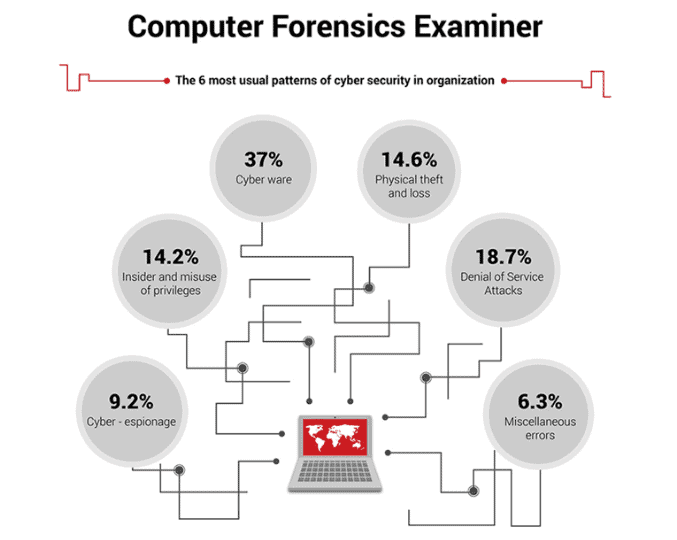
How do I get started with Computer Forensics Training?
You are about to take one of the most required training courses in the field of IT security. The PECB Computer forensics comprehensive training will provide you with outstanding skills that will help you to enhance your professional career. Our trainers are here to make sure that you achieve the goal of becoming a PECB Certified Professional on Computer Forensics.
PECB Certified Computer Forensics training courses available
The available PECB program of Computer Forensics provides training courses that will assist you in learning the key concepts and practices involved in computer forensics processes. Check below to find the training course that suits you best.
Who should attend?
- Individuals interested in Computer Forensics Processes
- Individuals seeking to gain knowledge about the main processes of Computer Forensics
- Individuals interested to pursue a career in Computer Forensics
Learning Objectives
- Understand the basic concepts of Computer Forensics
- Understand the basic processes of Computer Forensics
- Understand the approaches, methods and techniques used to effectively manage Computer Forensics Processes
Educational approach
- Lecture sessions are illustrated with practical questions and examples
- Practical exercises include examples and discussions
- Practice tests are similar to the Certificate Exam
Prerequisites
None
Course Agenda
Day 1: Introduction to Computer Forensics Processes
Day 2: Computer Forensics Processes and Certificate Exam
Examination
The exam fully meets the requirements of the PECB Examination and Certificate Programme. It covers the following competency domains:
Domain 1: Fundamental principles and concepts of Computer Forensics
Domain 2: Computer Forensics Processes
For specific information about exam type, languages available, and other details, please visit the List of PECB Exams and the Examination Rules and Policies.
General Information
- Certificate and examination fees are included in the price of the training course
- Training material containing over 200 pages of information and practical examples will be distributed
- An attestation of course completion worth 14 CPD (Continuing Professional Development) credits will be issued to the participants who have attended the training course.
- In case of exam failure, you can retake the exam within 12 months for free
Why should you attend?
Lead Computer Forensics Examiner training enables you to acquire the necessary expertise to perform Computer Forensics processes in order to obtain complete and reliable digital evidence. During this training course, you will also gain a thorough understanding of Computer Forensics fundamentals, based on the best practices used to perform forensics evidence recovery and analytical techniques. This training course is focused on core skills required to collect and analyze data from Windows, Mac OS X, and Linux operating systems, and also from mobile devices.
After mastering all the necessary concepts of Computer Forensics processes, you can sit for the exam and apply for a “PECB Certified Lead Computer Forensics Examiner” credential. By holding a PECB Lead Computer Forensics Examiner Certificate, you will be able to prove that you have the expertise to lead advanced forensic investigations and conduct forensics analysis, reporting, and evidence acquisition.
Who should attend?
- Computer Forensics specialists
- Computer Forensics consultants
- Cybersecurity professionals
- Cyber intelligence analysts
- Electronic data analysts
- Specialists in computer evidence recovery
- Professionals working or interested in law enforcement
- Professionals seeking to advance their knowledge in Computer Forensics analysis
- Information Security team members
- Information technology expert advisors
- Individuals responsible for examining media to extract and disclose data
- IT Specialists
Learning objectives
- Understand the roles and responsibilities of the Lead Computer Forensics examiner during digital forensic investigation
- Understand the purpose of electronic media examination and its correlation with common standards and methodologies
- Comprehend the correct sequence of steps of a computer incident investigation and digital forensic operation
- Understand the common commercial and open source tools that may be used during incident investigation and digital forensic operations
- Acquire the necessary competencies to plan and execute a computer forensics operation and also implement and maintain a safety network to protect evidence
Educational approach
- This training is based on both theory and best practices used in Computer Forensics
- Lecture sessions are illustrated with examples based on case studies
- Practical exercises are based on a case study which includes role playing and discussions
- Practice tests are similar to the Certification Exam
Prerequisites
Knowledge on Computer Forensics.
Course Agenda
Day 1: Introduction to Incident Response and Computer Forensics concepts
Day 2: Prepare and lead a Computer Forensics investigation
Day 3: Analysis and management of digital artifacts
Day 4: Case Presentation & Trial Simulation
Day 5: Certification Exam
Examination
The “PECB Certified Lead Computer Forensics Examiner” exam fully meets the requirements of the PECB Examination and Certification Programme (ECP). The exam covers the following competency domains:
Domain 1: Fundamental principles and concepts of Computer Forensics
Domain 2: Best practices on Computer Forensics
Domain 3: Digital forensics laboratory requirements
Domain 4: Operating system and file system structures
Domain 5: Mobile devices
Domain 6: Computer crime investigation and forensics examination
Domain 7: Maintaining chain of evidence
For specific information about exam type, languages available, and other details, please visit the List of PECB Exams and the Examination Rules and Policies.
Certification
After successfully completing the exam, you can apply for the credentials shown on the table below. You will receive a certificate once you comply with all the requirements related to the selected credential. For more information about Computer Forensics certifications and the PECB certification process, please refer to the Certification Rules and Policies.
To be considered valid, these computer forensics activities should follow best implementation practices and include the following:
- Conducting forensic investigation
- Post incident response activities
- Network management
- Computer forensics examination and analysis planning
- Analysis of file systems and digital media
- Forensics analysis of operating systems and networks
- Forensics analysis of computer and mobile devices
- Gathering digital evidence
General Information
- Certification and examination fees are included in the price of the training course
- Training material containing over 450 pages of information and practical examples will be distributed
- An attestation of course completion worth 31 CPD (Continuing Professional Development) credits will be issued to the participants who have attended the training course.
- In case of exam failure, you can retake the exam within 12 months for free







