What you know, what you have, and who you are;
These are three types of authentication. What you know, your password. What you have, a mobile device with a code through an authenticator app. And who you are, biometrics.
So why use it and how do I do so?
Access to shared file storage platforms in the cloud like MS OneDrive, Dropbox, MS Sharepoint, Box, and MS Teams..All of these applications offer two factor/multi-factor authentication, but why? Because having a password that you know, is not enough. With “what you have”, an authenticator app that sends a mobile code, you now have the ability to protect your login, if your password is compromised. Lastly, if you include the phone fingerprint to authenticate with the password, you have now enforced multi-factor authentication.
How it works:
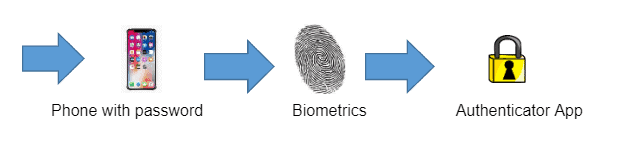
Most authenticator apps can register with any QR code, so choosing your app is sometimes an option, but other technologies for authentication must use the corresponding application to the software.
If you’re seeking government compliance through CMMC, hardening your mobile network is a requirement with very specific guidelines. Getting the ball rolling with two-factor authentication, to secure the connections to your mobile platforms, is a great start!







