CMMC has Changed Direction – the Department of Defense announced a significant change in direction while maintaining the goal of safeguarding sensitive information.

Why the Change?
“The Department values feedback from industry, Congress, and other stakeholders and received over 850 public comments in response to the interim rule establishing CMMC 1.0. These comments focused on the need to enhance CMMC by (1) reducing costs, particularly for small businesses; (2) increasing trust in the CMMC assessment ecosystem; and (3) clarifying and aligning cybersecurity requirements to other federal requirements and commonly accepted standards. CMMC 2.0 was designed to meet these goals, which also contribute toward enhancing the cybersecurity of the defense industrial base.”
Will Companies be required to comply with CMMC 1.0?
“The interim DFARS rule established a five-year phase-in period, during which CMMC compliance is only required in select pilot contracts, as approved by the Office of the Under Secretary of Defense for Acquisition and Sustainment (OUSD(A&S)). The Department does not intend to approve inclusion of a CMMC requirement in any contract prior to completion of the CMMC 2.0 rulemaking process.”
Once CMMC 2.0 is codified through rulemaking, the Department will require companies to adhere to the revised CMMC framework according to requirements set forth in regulation.
When will my organization be required to comply with CMMC 2.0?
“The publication of materials relating to CMMC 2.0 reflect the Department’s strategic intent with respect to the CMMC program; however, CMMC 2.0 will not be a contractual requirement until the Department completes rulemaking to implement the program. The rulemaking process and timelines can take 9-24 months. CMMC 2.0 will become a contract requirement once rulemaking is completed.”
How will my organization know what CMMC level is required for a contract?
“Once CMMC 2.0 is implemented, DoD will specify the required CMMC level in the solicitation and in any Requests for Information (RFIs), if utilized.”
What is the relationship between National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 and CMMC?
“Under CMMC 2.0, the “Advanced” level (Level 2) will be equivalent to the NIST SP 800-171. The “Expert” level (Level 3), which is currently under development, will be based on a subset of NIST SP 800-172 requirements.”
Will my organization need to be certified if it does not handle CUI?
“DoD’s intent under CMMC 2.0 is that if a DIB company does not process, store, or transmit Controlled Unclassified Information (CUI) on its unclassified network, but does process, store or handle Federal Contract Information (FCI), then it must perform a CMMC Level 1 self-assessment and submit the results with an annual affirmation by a senior company official into SPRS.”
What is the difference between a CMMC self-assessment, and a basic assessment required as part of the DoD Assessment Methodology?
A CMMC self-assessment will apply to those companies that are only required to protect the information systems on which FCI is processed, stored, or transmitted; and a subset of companies that are required to protect CUI. The CMMC self-assessment should be completed using the CMMC Assessment Guide codified in 32 CFR for the appropriate CMMC level. A CMMC self-attestation is a representation that the offeror meets the requirements of the CMMC level required by the solicitation. The CMMC program will require an annual self-assessment and an annual affirmation by a senior company official.
A “Basic Assessment”, as defined in DFARS clause 252.204-7020, NIST SP 800-171 DoD Assessment Requirements, means a contractor’s self-assessment of the contractor’s implementation of NIST SP 800-171 that —
- Is based on the Contractor’s review of their system security plan(s) associated with covered contractor information system(s);
- Is conducted in accordance with the NIST SP 800-171 DoD Assessment Methodology; and
- Results in a confidence level of “Low” in the resulting score because it is a self-generated score
What are the major changes from CMMC 1.0 to CMMC 2.0?
CMMC 1.0
CMMC 2.0
5 increasingly progressive levels from Basic to Advanced
- Levels 2 and 4 intended as transition stages between Levels 1, 3, and 5
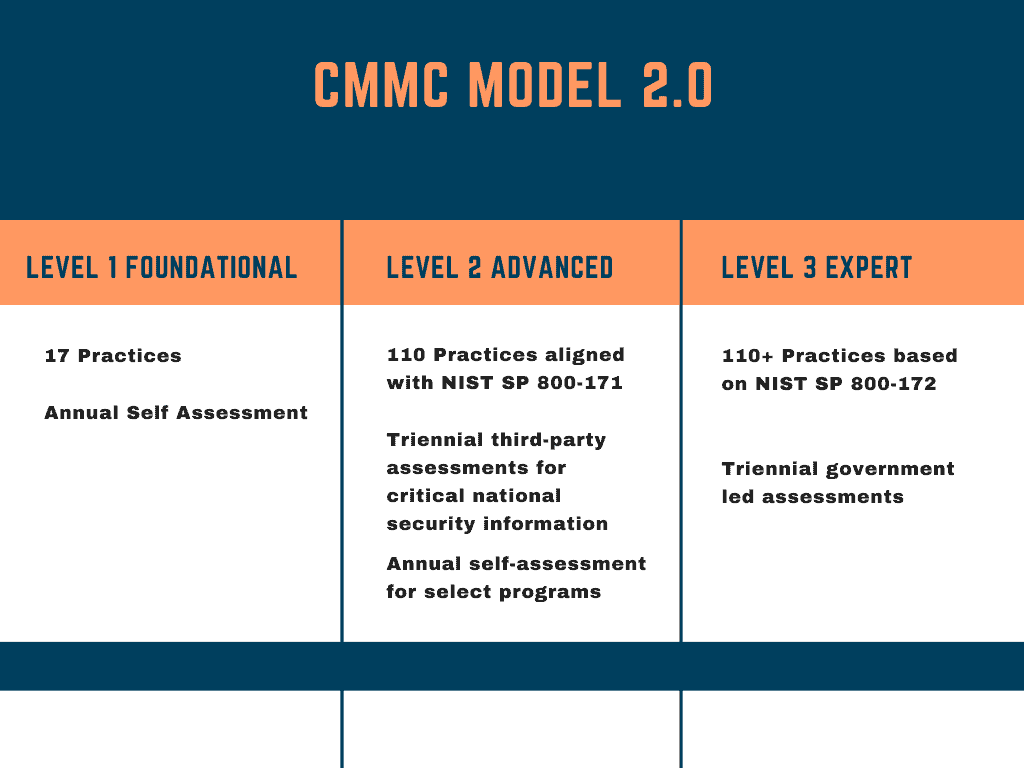
3 increasingly progressive levels:
- Foundational / Level 1 (same as previous level 1)
- Advanced / Level 2 (previous level 3)
- Expert / Level 3 (previous level 5)
- Requirements include cybersecurity standards and maturity processes at each level
- Cybersecurity standards consist of certain requirements from NIST SP 800-171 as well as CMMC-unique standards
- Eliminates all maturity processes
- Eliminates all CMMC unique security practices:
- Advanced / Level 2 will mirror NIST SP 800-171 (110 security practices)
- Expert / Level 3 will be based on a subset of NIST SP 800-172 requirements
- POA&M’s not allowed
- Allows the use of POA&M’s
- Highest weighted requirements cannot be on the POA&M List
- DoD Will Establish a minimum score requirement to support certification with POA&M’s
- Waivers not allowed
- Applied to entire CMMC requirement, not individual cybersecurity practices
- Allowed on a very limited basis in select mission critical instances, upon senior leadership approval
- DoD program office submits a justification package that includes specified timeline and associated risk mitigation plan
- Timelines imposed on a case-by-case basis to achieve CMMC compliance
- Assessments Required
- Allows most contractors, associated with Foundational/ Level 1 and a subset of Advanced/Level 2 programs, to perform annual self-assessments
- A portion of the Advanced/Level 2 programs will require triennial third-party assessments
- Expert / Level 3 programs will require triennial assessments conducted by government officials
- Oversight DoD Reviewed CMMC-AB Conflict of Interest Policies
- DoD will approve CMMC-AB’s Conflict of Interest policies
The framework has three key features:
Tiered Model
CMMC requires that companies entrusted with national security information implement cybersecurity standards at progressively advanced levels, depending on the type and sensitivity of the information. The program also sets forward the process for information flow down to subcontractors.
Assessment Requirement
CMMC assessments allow the Department to verify the implementation of clear cybersecurity standards.
Implementation through Contracts
Once CMMC is fully implemented, certain DoD contractors that handle sensitive unclassified DoD information will be required to achieve a particular CMMC level as a condition of contract award.
What’s new with CMMC 2.0
- The Maturity Levels are gone
- No C3PAO Assessment for Level CMMC 2.0 Level 1
- POA&Ms are not required for Level 1
- CMMC 1.0 Delta Practices are gone
- CMMC 2.0 Level 2 Assessments
- Initially the Majority of OSC’s will self-assess and self-attest
- OSC’s with CUI must be certified by a C3PAO
- POA&M’s will have limited scope and time requirements
- POAM’s will be enforced by the contract vehicle language
- CMMC 2.0 Level 2 Compliance with 32 CFR Part 2002 (CUI) & NIST SP 800-171







